A database view is a virtual table derived from...
TECHNOLOGY
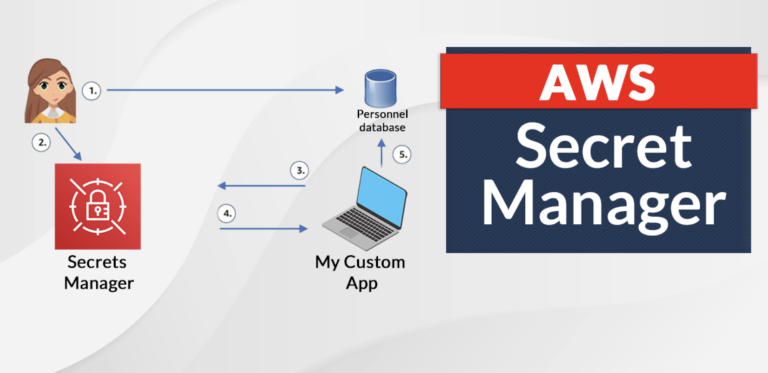
To integrate AWS Secret Manager with PHP using IAM...
Source Code Process: Grant merging access only to Team...
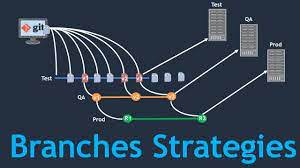
In any DevOps environment, version control is a crucial...
1. What steps would you take to handle a...
Converting a PPK (PuTTY Private Key) file to a...
Sunny Gupta’s journey from his early days in Chandigarh...
Here are the key benefits of gRPC: High Performance:...
Category: Identity and Access Management Category: Detection Category: Network...
Physical security in information security refers to the measures...