Introduction
A bastion host is an integral component of network security architecture that provides secure SSH access to private networks. With its exposed nature, a bastion host is a critical point that must be fortified to minimize penetration risks. Beyond providing access, it can also serve a vital auditing function by recording SSH sessions, which aids in regulatory compliance and incident analysis.
In this blog post, I will demonstrate how to leverage a bastion host in AWS to record SSH sessions securely and replay them for auditing purposes. The solution is straightforward, involves minimal configuration, and can be adapted for different use cases.
Solution Architecture
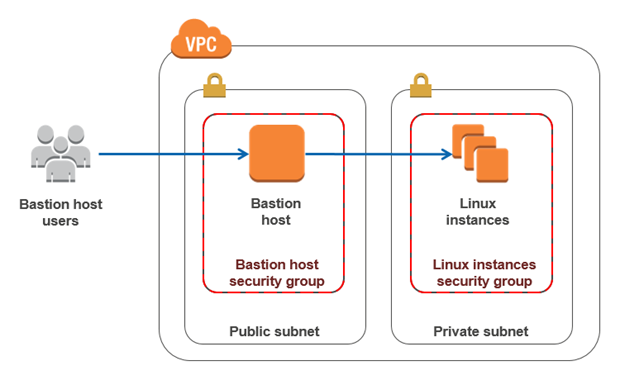
The architecture involves deploying a bastion host in a public subnet within an Amazon VPC to act as a gateway to instances in a private subnet. Here’s a high-level overview of the setup:
- Amazon VPC: A virtual private network hosts both the bastion host and private instances.
- Bastion Host: An Amazon EC2 instance in the public subnet allows SSH access to private instances. It is configured to record SSH sessions securely.
- Private Instances: These are in a subnet inaccessible from the internet and can only be accessed via the bastion host.
- Log Management: SSH session logs are stored in the bastion host and synced to an Amazon S3 bucket for durability and auditability.
The bastion host acts as the sole gateway for SSH traffic to private instances, ensuring centralized monitoring and control.
Implementation Details
1. Setting Up the Bastion Host
The bastion host is configured to record SSH sessions by modifying the sshd_config file to force the execution of a custom script. This script captures all input and output during the SSH session and saves it as log files.
Key commands include:
mkdir /var/log/bastion
chmod -R 770 /var/log/bastion
echo -e "\nForceCommand /usr/bin/bastion/shell" >> /etc/ssh/sshd_config
The custom script (/usr/bin/bastion/shell) wraps the interactive shell in a script command to capture session details.
2. Blocking Circumvention Methods
To prevent users from bypassing the recording mechanism, the following SSH features are disabled:
- TCP Forwarding: To block direct connections from local systems.
- X11 Forwarding: To disable GUI application forwarding over SSH.
Commands to enforce this include:
echo "AllowTcpForwarding no" >> /etc/ssh/sshd_config
echo "X11Forwarding no" >> /etc/ssh/sshd_config
service sshd restart
3. Managing SSH Session Logs
The session logs are stored in /var/log/bastion and are periodically synced to an S3 bucket for durability and compliance using a cron job.
cat > /usr/bin/bastion/sync_s3 << 'EOF'
aws s3 cp /var/log/bastion/ s3://bucket-name/logs/ --sse --region region --recursive && find /var/log/bastion/* -mtime +1 -exec rm {} \;
EOF
chmod 700 /usr/bin/bastion/sync_s3
4. User Account Management
To simplify user management, the bastion host periodically retrieves SSH public keys from an S3 bucket and creates or removes user accounts as needed.
- Public keys are uploaded to an S3 bucket folder (
public-keys/username.pub). - A script runs every 5 minutes to sync user accounts and public keys.
Example commands for user account synchronization:
cat > /usr/bin/bastion/sync_users << 'EOF'
# Script to manage user accounts based on public keys in S3
EOF
chmod 700 /usr/bin/bastion/sync_users
Testing the Solution
1. Setting Up Key Pairs
- Create two key pairs: one for the bastion host (
bastion.pem) and another for SSH users (sshuser.pem).
2. Deploying Resources with CloudFormation
Use AWS CloudFormation to provision resources, including the VPC, subnets, security groups, EC2 instances, and S3 bucket. Ensure the bastion host’s user data script includes all the configurations discussed.
3. Recording and Replaying Sessions
To test the recording mechanism:
- Connect to the bastion host using the
sshuser.pemkey pair with SSH agent forwarding:ssh -A sshuser@[bastion_host_public_IP] -i sshuser.pem - From the bastion host, connect to a private instance using its private IP:
ssh ec2-user@[private_instance_IP] - Run commands, exit, and replay the session log:
scriptreplay --timing=/var/log/bastion/[audit_key].time /var/log/bastion/[audit_key].data
Security Best Practices
- Restrict Key Pair Access: Limit access to the key pair associated with the bastion host. Consider launching the instance without a key pair and automating root-level operations.
- S3 Bucket Permissions: Use IAM policies to ensure only authorized users can access log files or upload public keys.
- User Privileges: Assign minimal privileges to bastion host users to prevent tampering with logs or configurations.
Conclusion
By implementing a bastion host to record SSH sessions, you enhance the security and auditability of your private network in AWS. This solution provides a centralized mechanism for monitoring SSH activity while ensuring compliance with regulatory requirements.
If you have any questions or feedback, feel free to share them in the comments below or join the discussion on the Amazon VPC forum.
Tags: Bastion Host, SSH Recording, AWS Security, Amazon VPC, EC2 Instance, Compliance, Network Security, Audit Logs, CloudFormation, S3 Bucket Management, Bastion Host, SSH Session Recording, AWS Security, Amazon VPC, Cloud Security, Audit Logs, AWS EC2, S3 Bucket, Compliance, Network Security