
Setting up SAML2 authentication with Laravel involves several steps. Here’s an outline of the process:
Install Required Packages: Start by installing the required packages in your Laravel project. Two popular packages for SAML2 integration are “spatie/laravel-saml” and “aacotroneo/laravel-saml2.” You can choose either package based on your preferences and requirements. Install the package using Composer.
Configuration: Configure the SAML2 settings in your Laravel application. This includes specifying the SAML2 service provider details, such as the identity provider (IdP) metadata URL, the entity ID, and the ACS (Assertion Consumer Service) URL.
Generate Metadata: Generate the SP (Service Provider) metadata for your Laravel application. This metadata will contain information about your application’s SAML2 configuration. You may need to expose this metadata URL to the identity provider so that it can establish a trust relationship.
Identity Provider Setup: Configure the identity provider (IdP) to establish trust with your Laravel application. This involves registering your application as a service provider (SP) in the IdP and providing the necessary metadata information.
Routes and Controllers: Create routes and controllers in your Laravel application to handle SAML2 authentication. These routes will be responsible for initiating the SAML2 authentication request, processing the response, and handling the authentication flow.
Views and UI: Build the necessary views and UI components to display the login button or link that triggers the SAML2 authentication process. You may also need to handle the user interface for displaying SAML2 errors or confirmation messages.
Testing and Debugging: Test the SAML2 authentication flow in your Laravel application. Use a SAML2 identity provider simulator or a real IdP to initiate the authentication process and ensure that the authentication flow is working correctly. Debug any issues or errors that may arise during the testing phase.
Additional Functionality: You can extend the SAML2 integration to include additional features such as user attribute mapping, role-based access control, or single logout functionality. These features may require additional configuration and customization based on your specific requirements.
Remember to consult the documentation and examples provided by the chosen SAML2 package for Laravel to understand the specific implementation details and any additional steps required for successful integration.
It’s worth noting that setting up SAML2 authentication can be complex, and it’s recommended to have a good understanding of SAML2 concepts and protocols before attempting the integration.

Here are the steps on how to set up SAML2 with Laravel:
Install the laravel-saml2 package.
composer require aacotroneo/saml2
Run the migrations.
php artisan migrate
Configure the SAML2 settings.
Open the app/config/saml2.php file and configure the following settings:
entityId: The entity ID of your SAML2 service provider.
assertionConsumerServiceUrl: The URL of your SAML2 service provider’s assertion consumer service.
singleLogoutServiceUrl: The URL of your SAML2 service provider’s single logout service.
idpMetadata: The metadata of the identity provider (IdP) that you want to use with your SAML2 service provider. You can get the IdP metadata from the IdP’s website.
Configure the IdP settings.
Open the app/config/saml2/idp_settings.php file and configure the following settings for each IdP that you want to use with your SAML2 service provider:
entityId: The entity ID of the IdP.
ssoUrl: The URL of the IdP’s single sign-on service.
logoutUrl: The URL of the IdP’s single logout service.
certificate: The certificate of the IdP. You can get the certificate from the IdP’s website.
Test the SAML2 configuration.
You can test the SAML2 configuration by visiting the following URL in your browser:
http://localhost/saml2/login
If the SAML2 configuration is correct, you will be redirected to the IdP’s login page. After you login to the IdP, you will be redirected back to your Laravel application.
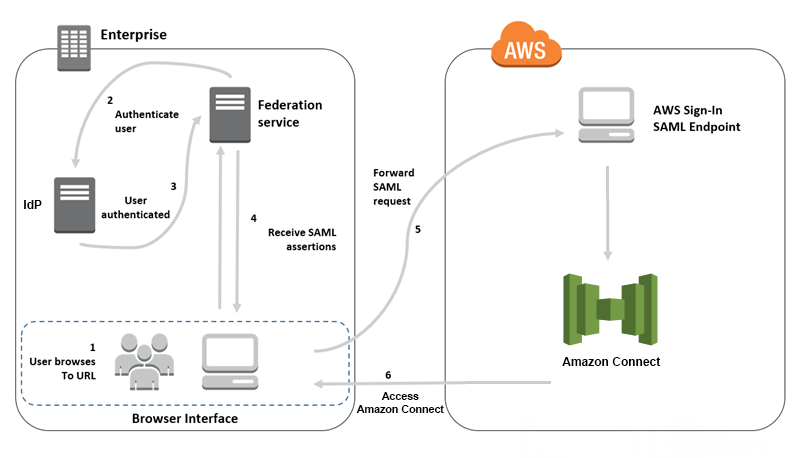
How SAML Works?
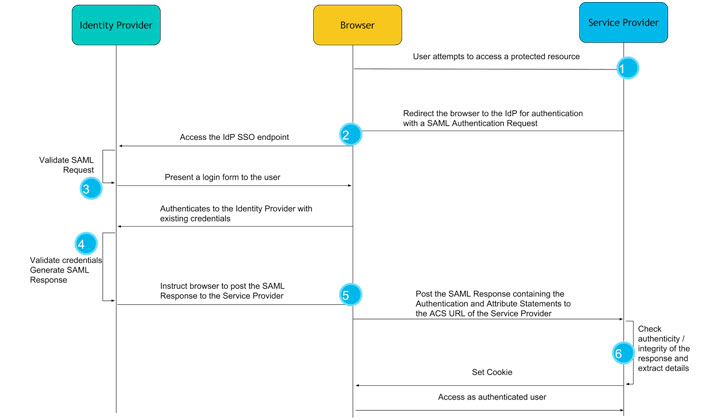
SAML (Security Assertion Markup Language) works based on a trust relationship established between the Identity Provider (IdP) and the Service Provider (SP). Here’s a step-by-step explanation of how SAML works:
- User Authentication Request: The user tries to access a service or application provided by the Service Provider (SP). The SP requests authentication from the user.
- Redirection to IdP: The SP generates a SAML authentication request and redirects the user’s browser to the Identity Provider (IdP).
- User Authentication at IdP: The user enters their credentials (e.g., username and password) at the IdP’s login page.
- SAML Assertion Generation: Once the user is authenticated, the IdP generates a SAML Assertion. This assertion contains information about the user’s identity and attributes, such as name, email, roles, etc. The assertion is digitally signed by the IdP to ensure its integrity.
- SAML Response: The IdP sends the SAML Assertion back to the user’s browser as a SAML Response.
- Submission to SP: The user’s browser submits the SAML Response to the SP.
- Assertion Validation: The SP verifies the authenticity and integrity of the SAML Assertion by validating the digital signature of the IdP. It also checks if the assertion is issued by a trusted IdP.
- User Session Creation: If the SAML Assertion is valid, the SP extracts the user’s identity and attributes from the assertion and creates a session for the user. The user is now authenticated and can access the requested service or application.
Throughout this process, the SAML protocol ensures the secure exchange of authentication information between the IdP and the SP. The use of XML-based SAML Assertions allows for the standardized representation and transfer of user identity data.
SAML is widely used in scenarios where there is a need for single sign-on (SSO) and federated identity management across multiple systems or organizations. It provides a secure and interoperable way to authenticate users and share their identity information between trusted parties.
SAML and Single Sign-On (SSO)
That’s correct! SAML (Security Assertion Markup Language) is often used in the context of Single Sign-On (SSO) scenarios. SSO enables users to log in once and access multiple applications or services without the need to provide their credentials repeatedly.
In the case of SAML-based SSO, both IdP-initiated and SP-initiated authentication workflows are possible:
- IdP-Initiated Authentication: In this scenario, the user is already authenticated with the Identity Provider (IdP). When the user tries to access a Service Provider (SP), the IdP automatically generates a SAML assertion containing the user’s identity information and redirects the user’s browser to the SP. The SAML assertion is sent along with the redirect, allowing the user to be automatically logged in to the SP without entering their credentials again.
- SP-Initiated Authentication: In this scenario, the user tries to access a resource or service provided by the SP. The SP recognizes that the user is not authenticated and redirects the user’s browser to the IdP’s SSO login page. The user then enters their credentials (username and password) at the IdP’s login page. After successful authentication, the IdP generates a SAML assertion, which is sent back to the SP. The SP validates the SAML assertion and logs the user in, granting access to the requested resource.
In both cases, SAML assertions are used to securely exchange authentication and authorization information between the IdP and the SP, allowing for seamless and secure SSO across multiple applications or services.
SSO with SAML offers convenience for users as they don’t need to remember and enter separate credentials for each application. It also simplifies user management and improves security by centralizing authentication and authorization controls within the IdP.
SAML 2.0 Benefits and Use Cases
Implementing the SAML 2.0 protocol offers several benefits and can be advantageous for various use cases. Here are some key benefits of using SAML 2.0:
- Standardization: SAML is an open standard, widely adopted across different platforms and applications. This standardization ensures interoperability between systems, making it easier to integrate and exchange authentication and authorization information.
- Improved User Experience: SAML enables Single Sign-On (SSO), allowing users to authenticate once and access multiple Service Providers (SPs) without the need for repeated logins. This streamlined login process enhances the user experience by eliminating the need for multiple credentials and reducing friction when accessing different applications or services.
- Loose Coupling of Directories: SAML separates user authentication from user attribute management. User information is maintained and synchronized within the Identity Provider (IdP), eliminating the need to duplicate and synchronize user data across multiple directories or systems. This loose coupling reduces complexity and maintenance overhead.
- Enhanced Security: SAML provides a centralized and secure authentication process through the IdP. User credentials are not replicated or stored across different SPs, minimizing the attack surface for potential security breaches. SAML also supports strong authentication mechanisms, such as multi-factor authentication, to further enhance security.
- Cost Savings for Service Providers: By implementing SAML, Service Providers can offload the responsibility of user account management to the IdP. This reduces the overhead of maintaining user accounts and associated password management across multiple services, resulting in cost savings for the SP.
- Compliance and Data Privacy: SAML supports the exchange of user attributes between the IdP and SPs. This allows for on-the-fly attribute sharing, eliminating the need to create shadow accounts or duplicate user data in different systems. This approach aligns with data privacy regulations and reduces liability by minimizing the storage and retention of user data.
Overall, SAML 2.0 provides a standardized, secure, and efficient way to enable SSO and exchange user authentication and attribute information across different applications and systems, offering benefits in terms of interoperability, user experience, security, cost savings, and compliance.
Where Does Your Identity Platform (IdP) Fit with SAML 2.0 and Single Sign-On?
Auth0 is an identity platform that can greatly simplify the implementation of SAML 2.0 and Single Sign-On (SSO) in your application. Auth0 serves as an identity partner, providing a secure and user-friendly solution for integrating SAML authentication.
By using Auth0’s Universal Login feature, you can easily configure SAML authentication and offer it to your enterprise customers. With Auth0 handling the complexities of SAML, you can ensure a secure implementation without the risk of leaving vulnerabilities in XML signatures or encryption.
Auth0 can function as both the Identity Provider (IdP) and the Service Provider (SP), offering flexibility in how you integrate SAML into your application. When you use Auth0 as an IdP, your users will be redirected to Auth0’s login page to authenticate. Auth0 supports various authentication connections, including social providers, databases, LDAP directories (like Active Directory), and other SAML IdPs.
When your application needs to communicate with a SAML SP using Auth0, Auth0 acts as a mediator. It translates the application’s requests into a SAML Authentication Request and forwards it to the designated SAML IdP. Auth0 abstracts the underlying protocols, allowing you to seamlessly interact with different protocols while communicating with Auth0.
One of the advantages of using Auth0 as your Identity-as-a-Service (IdaaS) provider is the ability to offer users multiple Identity Providers. Auth0 supports integration with various IdPs, allowing users from different organizations to log in with their preferred credentials, such as G-Suite, while others can use a database connection or other supported authentication methods.
For SaaS businesses targeting enterprise customers, offering SAML 2.0 along with other protocols like OAuth and OpenID Connect demonstrates flexibility and compatibility with existing enterprise authentication systems. This enables you to cater to customers who have been using SAML for years and shows your commitment to meeting their specific needs.
By leveraging Auth0 as your identity platform, you can simplify the implementation of SAML 2.0, enhance security, and provide a seamless and customizable authentication experience for your users.





