In a SAML web browser single sign-on (SSO) scenario, the flow involves three main actors: the end user, the identity provider (IdP), and the service provider (SP). Here’s a breakdown of how the SAML web SSO flow works:

- User initiates authentication: The user attempts to access a protected resource on the service provider’s website or application.
- Redirect to the IdP: The service provider detects that the user is not authenticated and redirects them to the identity provider’s login page.
- User authentication: The user enters their credentials (username and password) on the identity provider’s login page.
- SAML assertion generation: Upon successful authentication, the identity provider generates a SAML assertion. This assertion contains information about the user, such as their identity, attributes, and authentication details. The SAML assertion is digitally signed by the identity provider to ensure its integrity.
- SAML response to the service provider: The identity provider sends the SAML assertion back to the service provider in a SAML response. The response may also include additional information, such as the user’s roles or group memberships.
- SP validates the SAML response: The service provider validates the digital signature on the SAML response to ensure its authenticity and integrity. It also checks the validity and expiration of the SAML assertion.
- User session creation: If the SAML response is valid, the service provider creates a user session and grants access to the requested resource. The user is considered authenticated by the service provider.
- Access to additional resources: Once the user has an active session with the service provider, they can access other protected resources within the same service provider without the need for further authentication.
Key components involved in SAML web browser SSO:
- Identity Provider (IdP): The identity provider is responsible for authenticating users and generating SAML assertions containing user information.
- Service Provider (SP): The service provider hosts the web applications or resources that users want to access. It relies on the identity provider for user authentication and receives SAML assertions to establish the user’s identity.
- SAML Assertion: It is an XML-based document issued by the identity provider, containing user identity, attributes, and authentication statements. The SAML assertion is digitally signed to ensure its integrity.
Benefits of SAML web browser SSO:
- Simplified user experience: Users only need to authenticate once with the identity provider, and subsequent access to various service providers is seamless.
- Centralized identity management: Identity providers serve as a central point for user authentication, allowing organizations to manage user identities, credentials, and access control from a single location.
- Enhanced security: SAML assertions are digitally signed, ensuring the integrity and authenticity of user information. User credentials are not shared with individual service providers, reducing the risk of unauthorized access.
- Scalability and interoperability: SAML is an open standard that enables interoperability between different systems and platforms, allowing organizations to integrate various service providers and identity providers.
SAML web browser SSO is widely used in enterprise environments where users need to access multiple web applications with a single set of credentials. It provides a secure and convenient way to authenticate users and share identity information across different systems while offering a seamless user experience.
SAML 2.0 Web Browser Single-Sign-On (SSO) is a specific implementation of the SAML 2.0 protocol that enables seamless authentication and authorization across multiple websites or applications. It allows users to log in once and access multiple web-based resources without the need for repeated authentication.
Here’s a step-by-step overview of how SAML 2.0 Web Browser SSO works:
- User initiates authentication: The user attempts to access a protected resource on a Service Provider (SP) application. Since the user is not yet authenticated, the SP redirects them to the Identity Provider (IdP) for authentication.
- IdP authentication request: The SP sends an authentication request to the IdP, requesting the user’s authentication.
- User authentication: The IdP presents a login page to the user, prompting them to enter their credentials (e.g., username and password).
- IdP generates SAML assertion: Upon successful authentication, the IdP generates a SAML assertion containing information about the user, such as their identity, attributes, and authentication details. The assertion is digitally signed to ensure its integrity.
- SAML response to SP: The IdP sends the SAML assertion back to the SP in a SAML response.
- SP validates the SAML response: The SP verifies the digital signature on the SAML response to ensure its authenticity. It also checks the validity and integrity of the SAML assertion.
- User session creation: If the SAML response is valid, the SP creates a user session, allowing the user to access the requested resource.
- Access to additional resources: Once the user has an active session, they can access other protected resources within the same SP or other SPs that trust the same IdP. The SP uses the SAML assertion to authorize the user’s access to these resources without requiring further authentication.
Key components involved in SAML 2.0 Web Browser SSO:
- Identity Provider (IdP): The IdP is responsible for authenticating users and generating SAML assertions containing user information.
- Service Provider (SP): The SP hosts the web applications or resources that users want to access. It relies on the IdP for user authentication and authorization.
- SAML Assertion: It is an XML-based document issued by the IdP, containing user identity, attributes, and authentication statements. The SAML assertion is digitally signed to ensure its integrity.
Benefits of SAML 2.0 Web Browser SSO:
- Single sign-on experience: Users only need to log in once to gain access to multiple applications, reducing the need for remembering multiple usernames and passwords.
- Centralized authentication and authorization: Authentication and authorization are handled by the IdP, providing a central point of control and management for user access across multiple SPs.
- Improved security: SAML assertions are digitally signed, ensuring the integrity and authenticity of user information. User credentials are not shared directly with each SP, reducing the risk of credential exposure.
- Seamless integration: SAML is an industry-standard protocol, enabling interoperability and compatibility across different systems and platforms.
SAML 2.0 Web Browser SSO is widely adopted in enterprise environments where users need to access multiple applications with a single set of credentials. It offers convenience, security, and simplified user management for organizations and provides a seamless user experience by eliminating the need for repeated logins across various applications.
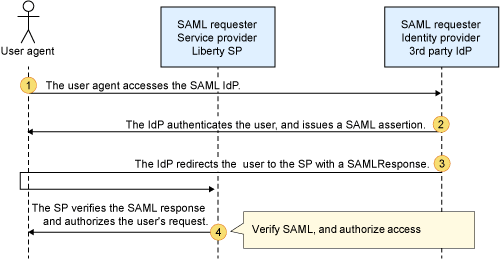
Key concepts in web Single Sign-On (SSO) can be summarized as follows:
- User Request for Service: The user initiates a request to access a service or resource provided by the service provider (SP). This could be a web application, a website, or any other online service.
- SP Requests User Identity: The service provider identifies that the user is not authenticated and needs to obtain the user’s identity. To do this, the SP redirects the user to the identity provider (IdP) via a redirect request.
- User Authentication: If the user is not already authenticated, the identity provider prompts the user to sign in and provide their credentials (username and password). This authentication process typically happens on the IdP’s login page.
- SAML Assertion Generation: Upon successful authentication, the identity provider generates a Security Assertion Markup Language (SAML) assertion. This assertion contains information about the user, such as their identity, attributes, and authentication details. The SAML assertion is typically digitally signed by the IdP to ensure its integrity.
- SP Receives SAML Assertion: The identity provider sends the SAML assertion back to the service provider in response to the redirect request. The SP receives the SAML assertion and begins the process of verifying its authenticity and integrity.
- Access Control Decision: Once the SAML assertion is validated by the service provider, it uses the information within the assertion to make an access control decision. The SP determines whether the user is authorized to access the requested service or resource based on the user’s identity and attributes provided in the SAML assertion.
By following this flow, web Single Sign-On allows users to access multiple services or resources without having to authenticate separately for each one. The SSO process relies on the exchange of SAML assertions between the identity provider and service provider to establish and verify the user’s identity.
It’s important to note that the SAML protocol is just one of the many protocols and technologies used for web SSO. Other popular protocols include OAuth, OpenID Connect, and CAS (Central Authentication Service). The choice of protocol depends on the specific requirements and systems involved in the SSO implementation.
Liberty SAML Web Browser SSO Scenarios
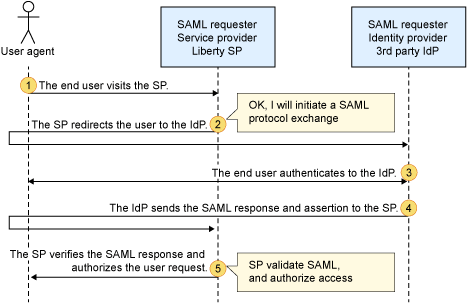
In the SP-Initiated solicited Web SSO scenario, the end user initiates the SSO process by visiting the service provider (SP) and requesting access to a protected resource. Here is a step-by-step explanation of the scenario:
- End User Visits SP: The end user accesses the SP’s website or application.
- SP Redirects User to IdP: The SP identifies that the user is not authenticated and needs to obtain the user’s identity. It generates a SAML request and redirects the user to the identity provider (IdP) with the request.
- End User Authenticates to IdP: The user is redirected to the IdP’s login page, where they are prompted to enter their credentials (username and password) to authenticate themselves.
- IdP Sends SAML Response: Upon successful authentication, the IdP generates a SAML response and SAML assertion. The SAML response contains the user’s authentication status, while the SAML assertion contains information about the user’s identity and attributes. The IdP sends the SAML response and assertion back to the SP.
- SP Verifies SAML Response: The SP receives the SAML response from the IdP. It verifies the digital signature on the response to ensure its authenticity. The SP also checks the validity and integrity of the SAML assertion contained within the response.
- Authorization and User Access: After verifying the SAML response and assertion, the SP makes an access control decision based on the user’s identity and attributes. If the user is authorized to access the requested resource, the SP grants access and proceeds with serving the requested content or functionality.
In this scenario, the SSO process is initiated by the end user visiting the SP. The SP then redirects the user to the IdP for authentication. Once the user is authenticated, the IdP sends the SAML response and assertion back to the SP, which verifies the response and grants access if authorized.
It’s important to note that this is just one specific scenario of SAML Web Browser SSO, and there are other variations and configurations depending on the specific requirements and configurations of the SP and IdP involved.
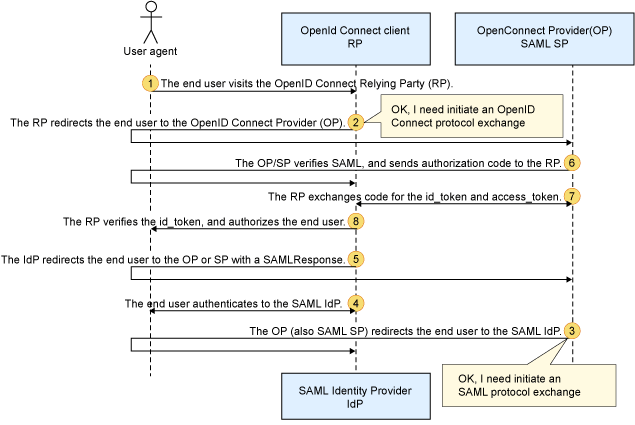
In the scenario you described, the end user interacts with both an OpenID Connect provider (OP) and a SAML service provider (SP) to authenticate and access resources. Here are the steps involved in this scenario:
- End User Visits RP: The end user visits the OpenID Connect Relying Party (RP), which is the application or service they want to access.
- RP Redirects User to OP: The RP identifies that the user needs to authenticate and redirects them to the OpenID Connect Provider (OP) for authentication. The redirection is typically done through the authorization endpoint of the OP.
- OP Redirects User to SAML IdP: Upon receiving the user’s request for authentication, the OP (which also acts as a SAML SP) redirects the user to the SAML Identity Provider (IdP) for authentication. This redirection is typically done through a SAML request sent to the IdP.
- End User Authenticates to SAML IdP: The user is redirected to the SAML IdP’s login page, where they provide their credentials to authenticate themselves.
- IdP Redirects User to OP/SP with SAMLResponse: After successful authentication, the SAML IdP generates a SAMLResponse containing the user’s authentication status and attributes. The IdP then redirects the user back to the OP or SP, passing the SAMLResponse.
- OP/SP Verifies SAML and Sends Authorization Code: Upon receiving the SAMLResponse, the OP or SP validates the SAMLResponse’s digital signature and checks its integrity. If the verification is successful, the OP or SP sends an authorization code to the RP.
- RP Exchanges Code for id_token and access_token: The RP receives the authorization code from the OP or SP and exchanges it for an id_token and access_token using the token endpoint of the OP.
- RP Verifies id_token and Authorizes User: The RP validates the received id_token to ensure its authenticity and integrity. It verifies the user’s identity and attributes contained in the id_token and authorizes the user to access the requested resources.
In this scenario, the end user interacts with the RP, which redirects them to the OP for authentication. The OP, acting as both an OpenID Connect provider and a SAML service provider, redirects the user to the SAML IdP for authentication. After successful authentication, the user is redirected back to the OP or SP with a SAMLResponse, which is verified by the OP or SP. The authorization code is then sent to the RP, which exchanges it for an id_token and access_token. The RP verifies the id_token and authorizes the user.
It’s important to note that this scenario combines the usage of both OpenID Connect and SAML protocols to achieve authentication and authorization. The specific implementation and configurations may vary depending on the OP, SP, and RP involved, as well as the specific requirements of the system.





